The IP Protocol
Tom Kelliher, CS 325
Apr. 13, 2011
Written assignment due in Friday.
Read 4.5-6.
Introduction to network layer protocols.
- Introduction.
- Network addressing.
- IP address management: DHCP and NAT.
- IPV6.
Project day;
Routing.
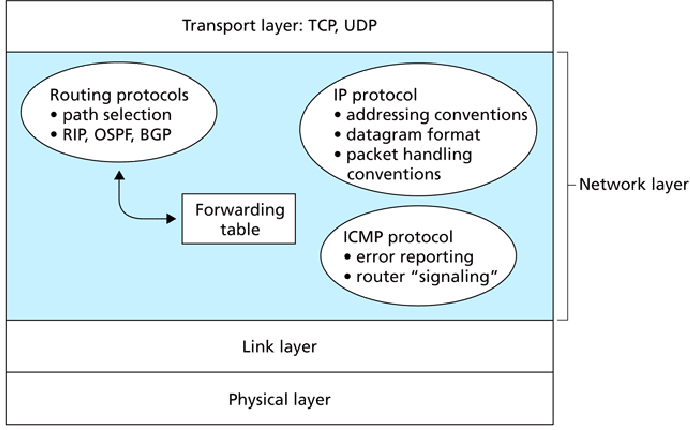
Network layer protocols:
- IP: datagram protocol.
Header:
Selected header fields:
- Version -- V4 or V6.
- Identifier -- sequence number.
- Flags, fragmentation offset: for fragment reassembly.
- Time-to-live (TTL) -- number of router hops remaining.
(Used by traceroute.)
- Protocol -- identifies transport layer protocol to route datagram
to (TCP or UDP).
- Source and destination IP addresses.
- ICMP: Internet Control Message Protocol.
Control messages sent as IP datagrams, with Protocol field set to ``ICMP.''
Sample messages:
- Echo request/reply (ping).
- Destination host/network/protocol/port unreachable.
Port unreachable refers to UDP -- a kluge?
- Destination host/network unknown.
- Router advertisement/discovery.
- TTL expired.
- Routing:
- Intra-AS: RIP, OSPF.
- Inter-AS: BGP.
Fragmentation:
- What happens if a datagram's size exceeds a link's MTU?
Split it into fragments!
- Downstream routers then route the fragments.
- Destination host re-assembles fragments into the original datagram.
Example: 4,000 byte datagram (20 bytes header; 3,980 bytes data) being sent
across a link with an MTU of 1,500 bytes.
| Fragment |
Data Bytes |
Offset |
Flag |
| 1st Fragment |
1,480 |
0 |
1 |
| 2nd Fragment |
1,480 |
185 (
 ) ) |
1 |
| 3rd Fragment |
1,020 (
 ) ) |
370 (
 ) ) |
0 |
Notes:
- Each datagram contains a 20 byte header.
- Each fragment uses the original datagram's identifier field.
- The offset is the eight byte offset from the beginning of the
original datagram of the first byte of the fragment.
Hence, all fragments, save the last, must have a data length that is a
multiple of 8.
- Flag = 0 means additional fragments. Flag = 1 means this is the
final fragment.
- The fragmentation mechanism permits fragments to be further
fragmented, with due care.
- Obviously, only complete datagrams are passed up to transport layer.
IP addresses are in ``dotted-decimal'' form:
Each host/router on a network has its own IP address:
- By definition, routers connect several networks. Hence, they have
multiple IP addresses.
- All hosts on the same network have the network portion of their IP
address in common.
IP addresses are hierarchical: network/host-on-network.
The network portion of these three networks:
![\includegraphics[width=4in]{Figures/fig04_16.eps}](apr13img9.png)
- The /24 specifies the netmask, or network portion of the IP
address: 255.255.255.0 -- 24 leading 1's.
The network portion of the IP address is the first 24 bits. The remaining
8 bits is the host portion of the IP address.
- A /20 corresponds to a netmask of 255.255.240.0 -- 20 leading
1's.
- /17 = 255.255.128.0; /18 = 255.255.192.0; /22 = 255.255.252.0; /23 =
255.255.254.0.
192 = 128 + 64; 252 = 128 + 64 + 32 + 16 + 8 + 4.
- /n addressing is referred to as CIDR -- Classless Interdomain
Routing.
Another way of conserving IP addresses.
- CIDR replaced classful routing -- Class A (/8), Class B (/16), Class
C (/24).
- It was/is common for organizations to subnet IP address ranges to
create ``networks within a network.''
Example: You're given a 64 address range: 66.240.10.64/26.
- Note: Two IP addresses are reserved within each network -- The
network IP number itself (host portion all 0's) and the broadcast
address (host portion all 1's).
- You can create four subnets using a /28 netmask. The subnets are
66.240.10.64, 66.240.10.80, 66.240.10.96, and 66.240.10.112.
Each subnet has 16 IP addresses; 14 usable.
- You can create eight subnets using a /29 netmask. The subnets are
66.240.10.64, 66.240.10.72, 66.240.10.80, etc.
Each subnet has 8 IP addresses; 6 usable.
The links connecting routers are considered networks themselves:
Networks can be supernetted:
Fly-by-Night has 8 /23's which have been aggregated (supernetted) into a
single /20 for routing purposes.
Address aggregation helps reduce forwarding table size.
Organization 1 can change ISPs, keeping its IP addresses, so long as the
new ISP advertises a ``more specific'' network (/23 vs. /20):
Where do I get an IP address(es)...
- to create a public network? From your ISP.
- if I'm an ISP? From ARIN. Also, to get an ASN.
- if I need public access to a host from within an existing network?
Obtain public IP address from IT.
- If I don't need public access from within an existing network? From
DHCP.
(Dynamic Host Configuration Protocol)
- Typically uses private networks: 10.0.0.0/8 or 192.168.0.0/16.
Must also use NAT.
- DHCP server dynamically assigns IP addresses from pool. Assignments
are temporary -- leased.
- Each network needs a DHCP server or a DHCP relay agent (usually a
router).
- DHCP clients also typically receive netmask, gateway, DNS servers,
WINS servers, etc. info from DHCP server.
DHCP exchange:
- Client sends DHCP Discover message. Note src IP addr of 0.0.0.0
(``this host'') and broadcast dest IP addr of 255.255.255.255.
Hopefully, the transaction ID is unique.
- Server responds with a DHCP offer message. Dest IP addr must be
the broadcast addr, but sent to client's port address, using the client's
transaction ID.
Client might receive several offers.
- Client responds to one offer with a DHCP request message, repeating
the original offer's parameters.
- Server responds with a DHCP ACK message, confirming the request.
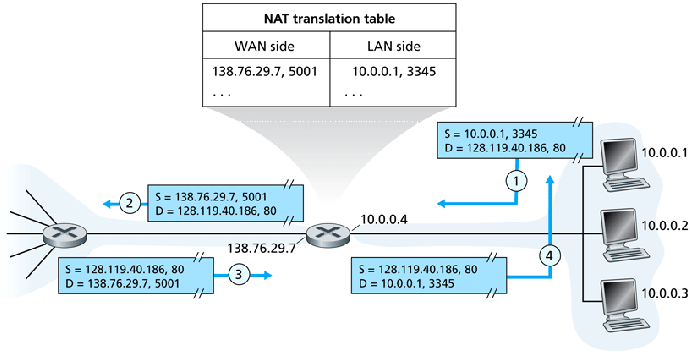
(Network Address Translation)
Comcast will give a residential customer one IP address (via DHCP). How
does the customer configure a home network? With NAT, and an internal DHCP
server!
NAT helps conserve IP addresses.
- Externally, a NAT router appears to handle only a single IP address
-- It's not really a router.
- Each device on the NAT network has its own IP address.
- The NAT router maintains a table of (external port, (local IP, local
port)) entries to handle the internal/external mapping of TCP and UDP
connections.
- As NAT routers look into the transport layer data, they're more than
just network layer devices.
- Provisions must be made for servers and P2P hosts behind NAT routers.
NAT translation example:
IPV6 header:
- Streamlined -- no options.
- No fragmentation -- easing burden on routers.
- No checksum -- again, easing burden on routers.
- Traffic class, flow -- to specify type of data (video stream,
interactive, etc.).
- Next header -- transport layer protocol.
- Hop limit -- TTL.
- Source and destination IP addresses -- 128 bits!!!.
Forwarding table lookups?
We're not going to be able to switch from IPV4 to IPV6 overnight.
IPV4 and IPV6 hosts/routers may have to interoperate for a period of time.
Two interoperation approaches:
- Dual stack:
Note that IPV6 characteristics get stripped.
- Tunnel:
Note that IPV6 datagrams are encapsulated in IPV4 datagrams.
Thomas P. Kelliher
2011-04-12
Tom Kelliher

![\includegraphics[width=5in]{Figures/fig04_13.eps}](apr13img2.png)
![\includegraphics[width=5in]{Figures/fig04_14.eps}](apr13img3.png)
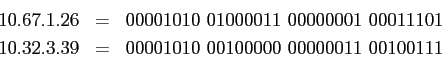
![\includegraphics[width=4in]{Figures/fig04_15.eps}](apr13img8.png)
![\includegraphics[width=4in]{Figures/fig04_16.eps}](apr13img9.png)
![\includegraphics[width=3in]{Figures/fig04_17.eps}](apr13img10.png)
![\includegraphics[width=5in]{Figures/fig04_18.eps}](apr13img11.png)
![\includegraphics[width=5in]{Figures/fig04_19.eps}](apr13img12.png)
![\includegraphics[width=5in]{Figures/fig04_20.eps}](apr13img13.png)
![\includegraphics[width=5in]{Figures/fig04_21.eps}](apr13img14.png)
![\includegraphics[width=5in]{Figures/fig04_24.eps}](apr13img16.png)

