Trusted Operating System Design I
Tom Kelliher, CS 325
Mar. 31, 2010
Read 5.3.
User authentication.
- Trust
- Security Policies
Security Models.
Operating systems enforce most of a system's security policies.
What is trust? How does one go about designing a trusted operating system?
Elements of the process:
- A stated security policy, as found in a requirements specification.
- A model to study the interaction of ``ordinary'' system functionality with
the security policy. Verify that all of the requirements
specification is adhered to.
- Design and implementation.
- Observation that the working operating system has the features necessary to
support the given security policy and development of confidence in those
features.
Typical software engineering?
There are degrees of trust, based upon:
- Enforcement of the given security policy.
- Sufficiency of measures and mechanisms.
- Evaluation -- sense of trust developed over time.
- Military -- centralized and hierarchical.
- Commercial -- no so centralized and hierarchical.
A mechanism for maintaining confidentiality.
- Sensitivity ranks: Unclassified, Restricted, Confidential, Secret,
Top Secret.
- Need to know rule: Access to sensitive data is allowed only to
subjects who need to know the data to perform their jobs.
- How do you prevent someone with Top Secret clearance from having
access to all data, then?
- Compartments (projects).
- Classification of an object, or clearance of an individual is
expressed as:
 .
.
Example:
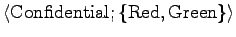 .
.
- For a given subject,
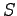 , to gain access to a given object,
, to gain access to a given object, 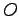 ,
, 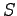 must dominate
must dominate 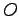 , as defined by:
, as defined by: 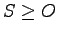 if and only if
if and only if
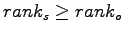 and
and
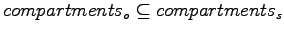 .
.
Can 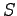 access
access 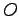 for each of the following?
for each of the following?
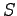 :
:
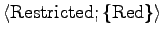 .
.
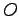 :
:
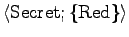 .
.
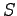 :
:
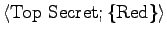 .
.
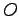 :
:
 .
.
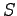 :
:
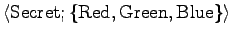 .
.
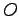 :
:
 .
.
A mechanism for maintaining integrity.
- A policy for well-formed transactions, maintaining integrity
between data items.
- The well-formed transactions themselves have an integrity property -- who
is authorized to perform them?
- Definitions:
- Constrained data item (CDI): data subject to integrity controls.
Example: Bank account balances.
- Integrity verification procedures (IVP): test CDIs to ensure they
conform to integrity guidelines.
Example: Confirming that accounts are balanced.
- Transformation procedures (TP): procedures that transform a set of
CDIs from one valid state to another.
Example: Transferring money from one account to another.
- A well-formed transaction captures all of this in a triple:
This is the idea of separating responsibilities so as to avoid the
possibility of fraud.
Example: In a business, more than one person should handle invoice receipt,
purchase confirmation, and check cutting.
A mechanism for ensuring confidentiality and the prevention of conflicts of
interest.
- Partition information (accounts) into conflict of interest sets.
Example:
- Set 1: Bank of America, M and T Bank, Wachovia Bank.
- Set 2: Mobil, Shell, Sunoco, Amoco.
- Once a subject accesses information from one element in a set, it may
not access information from any other element in that set.
Thomas P. Kelliher
2010-03-30
Tom Kelliher
![]() .
.
![]() access
access ![]() for each of the following?
for each of the following?
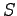 :
:
 .
.
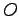 :
:
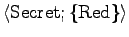 .
.
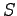 :
:
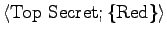 .
.
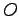 :
:
 .
.
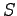 :
:
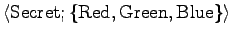 .
.
 :
:
 .
.
![]() .
.
![]() access
access ![]() for each of the following?
for each of the following?