Introduction to Ethics
Tom Kelliher, CS 200
Sept. 8, 2009
Read: Chapter 3.
Turn in answers to these questions: 12, 14.
Use a search engine to find, and turn in, a Web page relevant to: spam,
phishing, or spyware.
Introduction.
Networking.
- Morality vs. ethics and the purpose of this class.
- Ethical theories:
- Subjective and cultural relativism.
- Divine command theory.
- Kantianism and the Categorical Imperative:
- Act only from moral rules that you can at the same time will to
be universal moral laws.
- Act so that you always treat both yourself and other people as
ends in themselves and never only as a means to an end.
- Act utilitarianism.
- Evaluate each act's effect upon total ``happiness.''
- BJ Hunnicutt's affair in MASH. Hawkeye talks him out of
confessing the affair to his wife.
- ``Moral luck.'' Tediousness of the calculus.
- Rule utilitarianism.
- Society should adopt those moral rules which tend to increase
total ``happiness.''
- Same as Kantianism?
No. Kantianism focuses on will, motive, means. Utilitarianism
focuses consequences, end. ``The ends do not justify the means.''
- General problem: unjust distribution of ``happiness.''
- Social contract theory.
- Under what conditions would individuals abandon the state of
nature and enter into a civil society?
- ``Morality consists in the set of rules, governing how people
are to treat one another, that rational people will agree to accept,
for their mutual benefit, on the condition that others follow those
rules as well.
- The universalization clause of Kantianism does not apply --
only that the society accept a rule as binding.
- Rights: positive, negative, absolute, limited.
- Rawlsian justice:
- Claim to a ``fully adequate'' set of basic rights and
liberties.
- Any extant social or economic inequalities must: provide
fair equality of opportunity; benefit the least well-off in a
society.
- If you had to choose only one of these ethical systems for your own
use, which one would you choose? Why? How would you respond to the
arguments against the system?
- What are some examples of contemporary IT issues for which our
society's moral guidelines are unclear or nonexistent?
- Suppose that a society holds that it is wrong for an individual to
eavesdrop on the telephone conversations of another individual. Should that
stricture apply also to the society's government?
- John, a college student, frequently participates in YellowMUD. One
morning, the college's network administrator, Jane, arrives to find an
e-mail from YellowMUD's administrator, Sam, accusing John of severely
abusing several other YellowMUD participants and providing recorded scripts
of the event as proof. Sam has terminated John's YellowMUD account and
also demands that Jane terminate John's college network account. John
claims that Sam dislikes him, has been out to get him, and that the script
is a fabrication. Jane disables John's network account and refers the case
to the college's honor board. As a result, John can't complete required
coursework. John approaches Tom and asks him for assistance in the
defense. Tom agrees. Jane, not being very familiar with MUDs, their
surveillance capabilities, the feasibility of fabrication, nor how to
approach Sam for additional evidence, relies upon Tom's advice in
collecting information for the case. Has Jane behaved ethically in
immediately suspending John's account? Has Tom behaved ethically in
helping both sides?
- It is 1994 and the Web is just beginning to take off. Tom is an
assistant computer science professor at a small, rural, conservative,
religious-affiliated college. The college doesn't yet have its own Web
site. George, one of Tom's students, asks Tom for an independent study
project. Tom suggests that George set up a Web server on the department's
server and then begin to build a Web site for the college. Tom mentions
this idea to the college's IT director and all agree that it's a great
idea. A semester later, George has completed the Web site.
- One of the parts of the site is a listing of Web sites which might
be of interest to students. Tom notices that this listing includes a
link to a site called ``Condomania.'' He decides to ignore it. The
college's conservative culture would not support such a link, but Tom
reasons that this is something which could be of use to students. A
month later, Ralph, another faculty member, comes across this link while
browsing the Web site and points out its problematical nature to Tom.
Tom removes the link, later informing George of the deletion. George
doesn't object. On the two counts of initially allowing the link to
persist, and then later removing it himself rather than having George
remove it, has Tom acted ethically?
- Another part of the Web site contains smaller sites for the
college's sororities and fraternities.
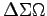 's Web site contains a page
of links to the fraternity's alumni's Web sites on various other Web
servers. Fred, one of the linked
's Web site contains a page
of links to the fraternity's alumni's Web sites on various other Web
servers. Fred, one of the linked
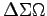 alumni, has a link to
pornography buried within his Web site. The college's development
director, Don, himself a
alumni, has a link to
pornography buried within his Web site. The college's development
director, Don, himself a
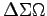 alumnus, discovers the pornography.
Several interested parties, including Don, Mike (a
alumnus, discovers the pornography.
Several interested parties, including Don, Mike (a
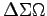 officer), and
Tom, meet to discuss the link. Don maintains that pornography
shouldn't be included in the college's Web site. Mike argues that
Fred's Web site isn't part of the college's site and that this is
censorship. Tom observes that from many ``safe'' Web pages it's
possible to reach pornographic content by following just a few links and
that most Web users understand that once they leave one Web site via a
link to another site, the first Web site is not expected to exert any
control of the second site's content. What should be done?
officer), and
Tom, meet to discuss the link. Don maintains that pornography
shouldn't be included in the college's Web site. Mike argues that
Fred's Web site isn't part of the college's site and that this is
censorship. Tom observes that from many ``safe'' Web pages it's
possible to reach pornographic content by following just a few links and
that most Web users understand that once they leave one Web site via a
link to another site, the first Web site is not expected to exert any
control of the second site's content. What should be done?
- Tom's taking an evening course offered by his company covering the
internals of its flagship mainframe operating system. To try out what's
he's learned, he decides to write a program to retrieve some information
deep within the operating system, a process which requires a good deal of
delicacy. If improperly accessed, the system might crash. In order to
actually run his program, he has to first run a special program to enable
his program. Access to the enabling program is usually only provided to
senior programmers. Tom runs his program on a heavily used production
mainframe, which typically has hundreds of engineers logged in. The
program behaves as expected. Has Tom done anything wrong?
Thomas P. Kelliher
2009-09-05
Tom Kelliher
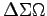 's Web site contains a page
of links to the fraternity's alumni's Web sites on various other Web
servers. Fred, one of the linked
's Web site contains a page
of links to the fraternity's alumni's Web sites on various other Web
servers. Fred, one of the linked
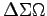 alumni, has a link to
pornography buried within his Web site. The college's development
director, Don, himself a
alumni, has a link to
pornography buried within his Web site. The college's development
director, Don, himself a
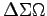 alumnus, discovers the pornography.
Several interested parties, including Don, Mike (a
alumnus, discovers the pornography.
Several interested parties, including Don, Mike (a
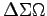 officer), and
Tom, meet to discuss the link. Don maintains that pornography
shouldn't be included in the college's Web site. Mike argues that
Fred's Web site isn't part of the college's site and that this is
censorship. Tom observes that from many ``safe'' Web pages it's
possible to reach pornographic content by following just a few links and
that most Web users understand that once they leave one Web site via a
link to another site, the first Web site is not expected to exert any
control of the second site's content. What should be done?
officer), and
Tom, meet to discuss the link. Don maintains that pornography
shouldn't be included in the college's Web site. Mike argues that
Fred's Web site isn't part of the college's site and that this is
censorship. Tom observes that from many ``safe'' Web pages it's
possible to reach pornographic content by following just a few links and
that most Web users understand that once they leave one Web site via a
link to another site, the first Web site is not expected to exert any
control of the second site's content. What should be done?