First presentation topic: PGP, including the basics of how it works and how
it is used today. Presentation on Sept. 15.
- Plain text, cipher text.
- Key.
- Interceptor aims: block, intercept, modify, fabricate.
- Symmetric cipher:
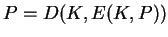 .
.
One key. Key distribution and management issues. Private key
cryptography.
- Asymmetric cipher:
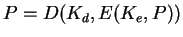 .
.
Two keys: private and public. Public key cryptography.
- Product Ciphers -- application of two or more ciphers:
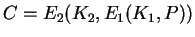 .
.
The result is not necessarily ``better.''
- Diffusion: A plain text character has a functional impact on multiple
cipher text characters.
This forces the cryptanalyst to have access to large amounts of cipher
text.
- Confusion: A cryptanalyst should not be able to predict the changes
that occur when one character of the plain text is changed. (Consider a
Caesar cipher.)
This property makes it harder to understand the relationship between the
plain text and the cipher text.
- Stream cipher: One plain text character is used to produce one cipher
text character.
Fast; no latency.
Poor diffusion; possibly little confusion.
- Block cipher: A block of plain text is used to produce a block of
cipher text.
Slower; latency.
Excellent diffusion and confusion.