the DNS and TCP
Tom Kelliher, CS43
Mar. 12, 1996
The /etc/hosts crisis.
A distributed database:
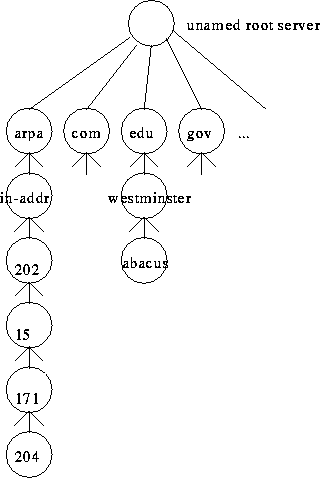
- Zones, zone files
- Primaries, secondaries; the SOA record
- Resolver routines, server
- Caching
- Address, pointer queries
- Hostname spoof check
Features:
- Unit of data is a segment.
- Connection-Oriented, full-duplex connection:
- A socket: (IP address, port number)
- A socket pair --- (client IP address, client port number1, server IP
address, server port number2) --- uniquely identifies a connection.
- Reliable:
- TCP breaks byte stream into ``best-sized'' chunks.
- Timer associated with each sent segment.
- Segment acknowldegements.
- TCP handles out of order IP datagrams, duplicate IP datagrams.
- Flow control --- window size.
- 16-bit source, destination port numbers.
- 32-bit sequence number.
- 32 bit acknowledgedment number.
- URG, ACK, PSH, RST, SYN, FIN.
- 16-bit window size.
- 16-bit TCP checksum.
Establishing a connection:
- Client sends SYN segment, specifying server port and initial sequence
number.
- Server sends SYN segment, including its initial sequence number and
ACKs the client segment.
- Client ACKs the server's SYN segment.
Active, passive open.
Terminating a connection (half-close):
- One side sends FIN segment.
- Other side sends ACK segment, sends EOF to application.
Active, passive close.
Establishment timeouts: 5s, 24s, 76s.
Window size, maximum segment size.
Looking at the connections on a Unix system:
- Port, host, interface wildcards.
- Connection State.
Sequence numbers:
- What are we numbering? Why?
- Initial sequence number. Why not start at 1?
- ISN counter should increment every 4 microseconds.
- ISN counter typically increment by 64,000 every half-second.
Due to poor randomization of ISNs.
- Disable client
- Spoof client's IP address, guess ISN of server.
- Can't see server segments, have to guess.
- Path MTU Discovery --- optimize packet size.
- Long Fat Pipes:
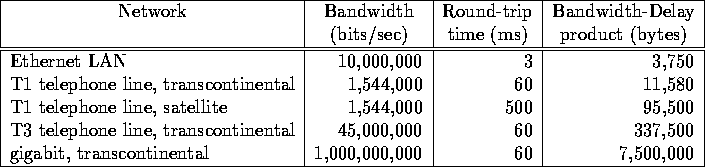
- Window scale option --- dealing with bandwidth-delay.
- Timestamp option --- RTT calculations.
- PAWS: Protection Against Wrapped Sequence number.
- T/TCP: an extension for transactions --- reduce the handshaking.
- Performance.
- Backward compatibility.
Thomas P. Kelliher
Tue Mar 12 11:08:43 EST 1996
Tom Kelliher


