Architectural Support for System Protection
Tom Kelliher, CS42
Sept. 9, 1996
Why?
What needs protection:
- The OS itself.
- Threads.
- Devices.
What developments made this protection necessary?
- Dual mode operation.
- Privileged I/O instructions.
- Memory protection mechanisms.
- Interval timers.
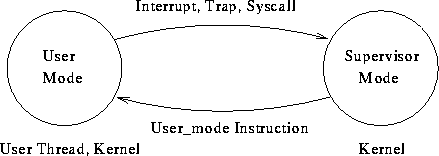
CPU operates in two or more states:
- Supervisor mode
- All instructions may be executed.
- This is a privileged mode.
- Only parts of the OS run in this mode.
- User threads never run directly in this mode.
- User mode
- Some instructions are ``privileged.''
- Attempt to execute a privileged instruction results in a trap.
- User threads execute in this mode.
Examples of privileged instructions:
- I/O instructions.
- Halt.
- Reset.
- Mask interrupts.
- Set interval timer.
- Set status. Read status?
- Modify page table registers.
Differences, similarities between interrupts, traps, system calls?
Schema of System operation:
- System powered on; in supervisor mode.
- System boots, kernel initializes, still in supervisor mode.
- System enters user mode to run user threads.
Should there be a user mode instruction to enter supervisor mode?
How can supervisor mode be re-entered?
Prevent thread from scribbling on arbitrary memory locations.
Mechanisms:
- Bounds registers:
- Base, limit registers.
- Base, length registers.
How does it work?
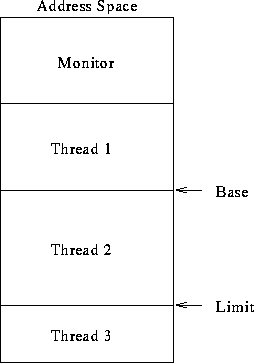
- Thread 2 running.
- All generated addresses checked against base, limit.
- ``Out-of-bounds'' addresses generate traps.
What needs to be done on a context switch?
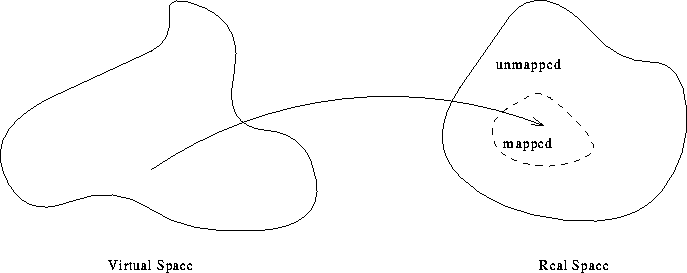
- Virtual memory --- threads run in individual ``virtual'' address
spaces.
Virtual address space mapped onto subset of physical address space:
What prevents a thread from grabbing the CPU and not relinquishing it?
Interval timer, interrupt. On context switch:
- Set interval time.
- Run user thread.
- Timer interrupt generated on timer expiration.
- Run timer interrupt handler.
Used to:
- Enforce timesharing quantum. Typical quantum: 100 ms.
- Keep time (?!?).
How does a process perform I/O if it's a privileged operation?
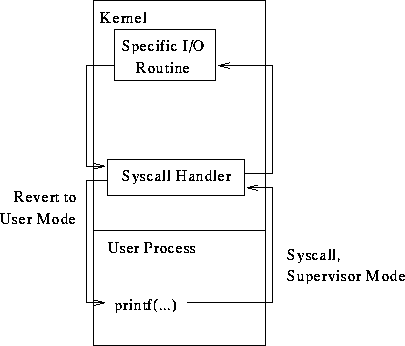
Question:
Unix has an abstraction of the interrupt, called a signal. A user
program can install its own signal handler. Interrupt handlers always run
in supervisor mode. Should a signal handler run in supervisor mode?
(Consider the consequences.)
Thomas P. Kelliher
Fri Sep 6 10:58:51 EDT 1996
Tom Kelliher




