Protection
Tom Kelliher, CS42
Nov. 25, 1996
Definition:
A mechanism for controlling the access of programs, processes, or
users to the resources defined by a computer system.
How good is this?
Examples from what we've already studied?
- Separate un-trustworthy entities.
- Control access to resources.
- Detect design flaws, malfunctioning subsystems.
- Provide flexible mechanisms for supporting a multitude of policies.
What's being protected: objects in the name space.
Need-to-know principle:
At any time, an object should only have access to those objects needed
to work toward the completion of its task.
Example: the root account on a Unix system.
Domain:
A set of access rights. An access right is an order pair,
<object-name, rights set>, stipulating what operations (rights
set)
may be applied to an object (object-name). An object works within one
domain at a time, with the possibility of switching domains.
- Static, dynamic domains.
- Static domains and need-to-know.
- The intersection of domains need not be empty.
Objects which may make use of domains:
- Users.
- Processes, threads.
- functions.
- Users switch between domains.
- su.
- Setuid.
abacus:~/Class/Cs42/Lectures
% ls -l `which xterm`
-rwsr-xr-x 1 root wheel 131072 Jan 2 1996 /usr/X11/bin/xterm*
- Setgid.
abacus:~/Class/Cs42/Lectures
% ls -l /usr/sbin/sendmail /usr/sbin/lpc
-r-xr-sr-x 1 bin daemon 16384 Jan 1 1996 /usr/sbin/lpc*
-r-sr-sr-x 3 root kmem 208896 Oct 12 16:42 /usr/sbin/sendmail*
- Problems with setuid programs:
- Shell escapes.
- Shell scripts.
- ``Safe'' setuid programs:
- Custom-written programs.
- Perl.
- Domains are hierarchical rings (0--7). Ring 0 highest privilege.
- Functions exist within domains.
- Processes change domains through function calls. Gating to provide
protection.
- Consequences wrt. need-to-know?
General model of a domain.
- Rows: domains.
- Columns: objects. Includes:
- Domains.
- The access matrix itself.
Entries:
- Standard access rights: read, write, execute, etc.
- Switch: switch from one domain to another.
- Copy: allows a right to be propagated to other domains (*).
Variations.
- Owner: a domain owns an object; may modify rights at will.
- Control: a domain controls another domain; may remove
any rights.
Example:
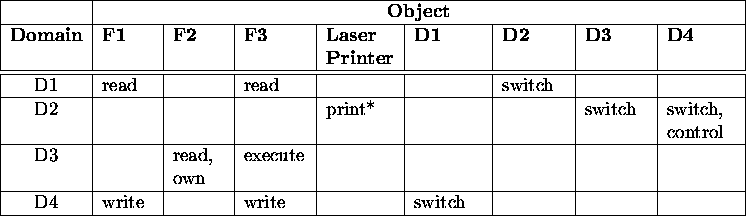
- Very sparse matrix.
- Global table: ordered triples <domain, object-name, rights set>.
Issues:
- Storage efficiency.
- Rights-checking efficiency.
- Ease of adding, revoking rights.
- List associated with each object.
- Order pairs: <domain, rights set>.
- Variation: Search access list on first access, receive and use
capability subsequently.
- List of ordered pairs, <object, rights> associated with a domain.
- Inaccessible to objects in the domain.
- A ``secure'' pointer.
- Revocation implementation:
- Expiration, reacquisition.
- Back-pointers.
- Indirection.
- Keys.
Example: kerberos(1).
- Combination of access list, capabilities.
- Keys associated with domain, object.
- Access permitted if a domain key matches an object key.
Thomas P. Kelliher
Mon Nov 25 09:24:08 EST 1996
Tom Kelliher

