Tom Kelliher, CS 318
Apr. 29, 1998
Announcements:
From last time:
Outline:
Assignment: Read Chapters 10 and 11.
From /usr/include/ufs/ufs/dinode.h:
#define NDADDR 12 /* Direct addresses in inode. */
#define NIADDR 3 /* Indirect addresses in inode. */
struct dinode {
u_short di_mode; /* 0: IFMT and permissions. */
short di_nlink; /* 2: File link count. */
union {
u_short oldids[2]; /* 4: Ffs: old user and group ids. */
ino_t inumber; /* 4: Lfs: inode number. */
} di_u;
u_quad_t di_size; /* 8: File byte count. */
struct timespec di_atime; /* 16: Last access time. */
struct timespec di_mtime; /* 24: Last modified time. */
struct timespec di_ctime; /* 32: Last inode change time. */
daddr_t di_db[NDADDR]; /* 40: Direct disk blocks. */
daddr_t di_ib[NIADDR]; /* 88: Indirect disk blocks. */
u_long di_flags; /* 100: Status flags (chflags). */
u_long di_blocks; /* 104: Blocks actually held. */
long di_gen; /* 108: Generation number. */
u_long di_uid; /* 112: File owner. */
u_long di_gid; /* 116: File group. */
long di_spare[2]; /* 120: Reserved; currently unused */
};

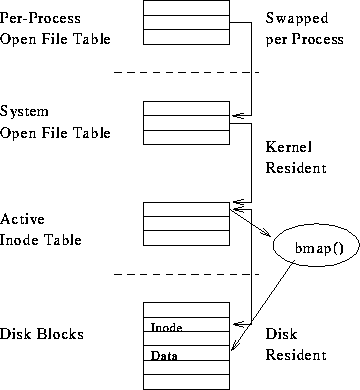
To be cached and re-used:
for each path component
find inode of directory
start reading data blocks (directory entries)
for each directory entry
found desired component?
Excessive time spent in namei(). Recent translations cache.
Structures:
Access:
Imposing order on the morass.
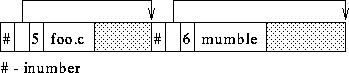
File naming restrictions: structure of a directory file.
Unix directory entries:
/home1/kelliher/Util /home1/kelliher/Util/I386 /usr/local/bin /bin /usr/bin /usr/X11/bin /usr/contrib/bin /usr/contrib/texmf/bin /sbin /usr/sbin /keystone/bin /keystone/decstation-ultrix/bin
Types:
Implementation: