Counterexample, Fixed-Network Connection Model
Tom Kelliher, CS 315
Feb. 8, 1999
Read Sections 1.2.1, 1.2.2.
Homework due 2/17: Problems 1.2, 1.3, 1.5, 1.7, 1.15.
Lower bound techniques, counterexample.
- The counterexample.
- Properties of the fixed-network connection model.
Carry-lookahead addition, parallel prefix computations.
Consider sorting within a complete binary tree:
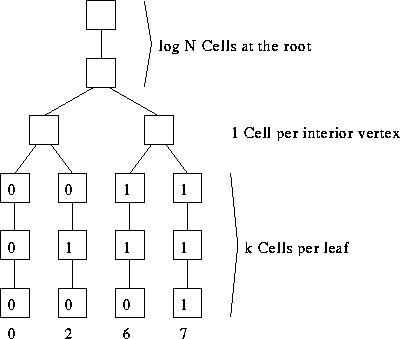
- Assumption: All
 bits appear simultaneously.
bits appear simultaneously.
- I/O bandwidth? Diameter? Bisection width?
- Lower bound for sorting on a binary tree?
- Almost right. Holds for
 .
.
- So, how do we beat the lower bound? By counting.
- Problem of unary to binary conversion.
- ``Easy'' if interior cells are word processors.
- Each interior processor need only be a serial adder and we do
bit-wise serial addition with numbers transmitted lsb-first.
Example: Bit-wise addition of 0110 and 0011.
- Example: counting the 1's when N = 8.
- Setting the leaf bits:
- Assume we have m 1's.
- Set the rightmost m leaves. Clear the leftmost N - m leaves.
- Observation: right 0 leaf is numbered N - 1 - m.
This is the bit-wise complement of m.
- Use N - 1 - m to find a path to that leave, clearing leaves to
the left, setting leaves to the right, and clearing that leave.
- Sorting can be done in
 . What does this tell
us?
. What does this tell
us?
- Don't forget: You're counting, not sorting.
- Processor properties:
- Local control.
- Computation is a function of local storage and local inputs.
- Variations. Processor might know such things as its address,
topology/size of the network, time.
Storage is usually constant, but may vary with size of network.
- A bit processor may perform a constant number of bit operations
per step. Similarly for a word processor.
- Limits on word size usually
 .
.
- Packets: indivisible communication data stamped with a key.
- Interconnection properties:
- Connections may not vary with time.
- A constant amount of communication (bits, words, packets, as
appropriate) can occur across a connection per step.
- Bounded-degree network. Sometimes degree will be O
 .
.
Size is polynomial in N.
- I/O protocol properties:
- Each input is provided only once.
- I/O is when and where oblivious: the time and location, for each
piece of data, of I/O must be specified in advance.
Without this restriction, we could sort in constant time.
- Comment: This model describes systolic VLSI very well. It doesn't
describe general VLSI well since we don't have ``long'' wires. But, how
does one model the communication properties of a long wire?
Thomas P. Kelliher
Mon Feb 8 07:57:37 EST 1999
Tom Kelliher


 bits appear simultaneously.
bits appear simultaneously.
 .
.
 . What does this tell
us?
. What does this tell
us?
 .
.
 .
.